Overview of Strong Authentication
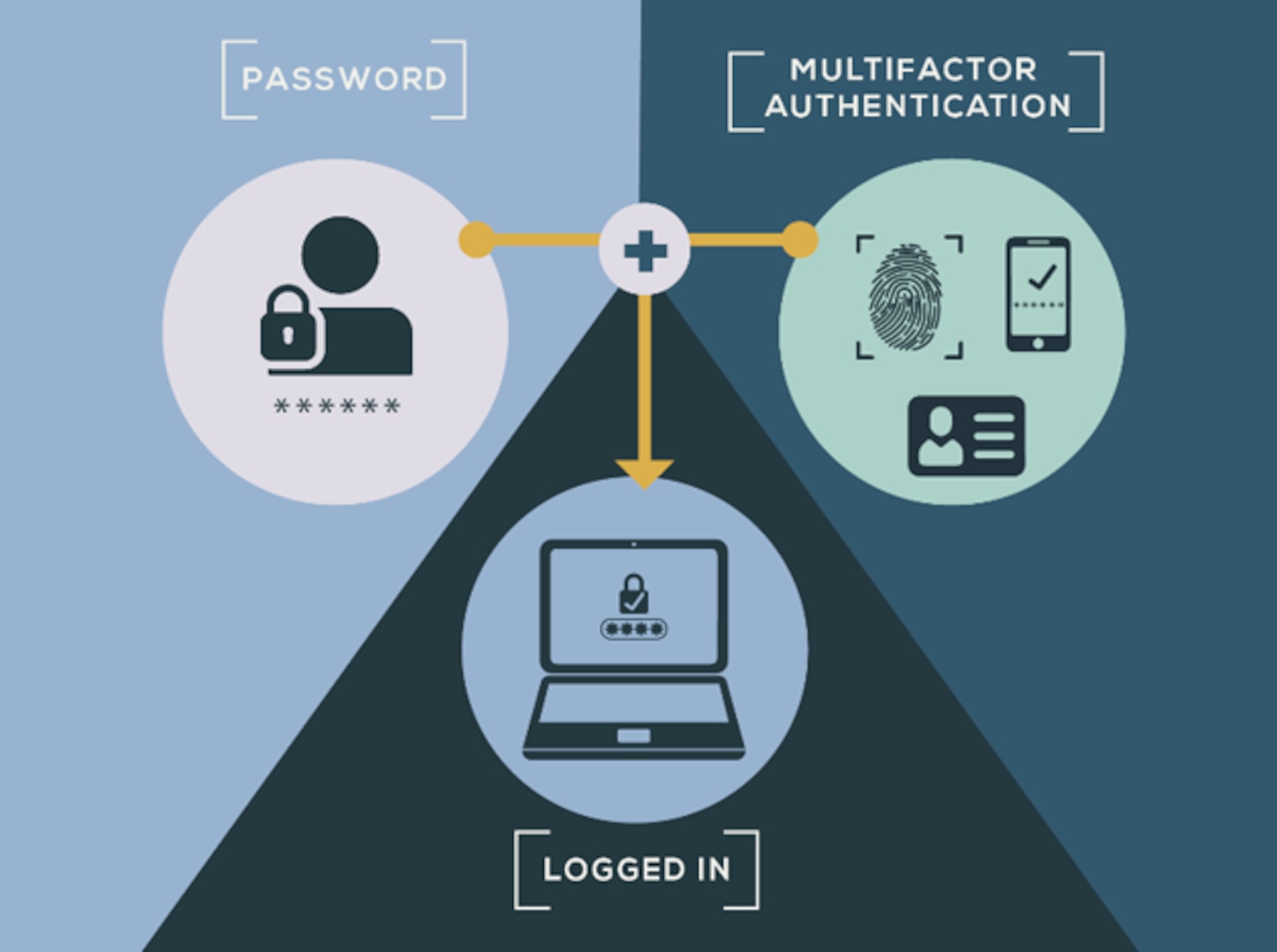
Strong authentication refers to security processes that require multiple forms of verification to confirm a user’s identity before granting access to systems or data. This approach goes beyond traditional password-based authentication by combining factors from different categories: something you know (password, PIN), something you have (security token, mobile device), and something you are (biometric data like fingerprints or facial recognition). The goal is to make unauthorized access significantly more difficult, even if one factor is compromised.
Password Policies: Best Practices
Passwords remain a foundational element of authentication, but their effectiveness depends on robust policies and secure handling.
Key Password Policy Recommendations:
- Complexity: Require passwords with a mix of uppercase, lowercase, numbers, and special characters.
- Length: Enforce a minimum length (typically 12 characters or more).
- Passphrases: Encourage the use of passphrases—longer, memorable phrases—instead of single words.
- Blacklists: Prevent the use of common or compromised passwords through blacklists.
- Storage: Never store passwords in plain text; use strong, slow hashing algorithms (e.g., bcrypt, Argon2, PBKDF2) with salting.
- Rotation: While frequent password changes are no longer universally recommended, periodic updates may still be warranted in high-risk environments.
- Account Lockout: Implement policies to lock accounts after repeated failed login attempts, with secure recovery options.
Two-Factor and Multi-Factor Authentication (2FA/MFA)
Two-factor authentication (2FA) and multi-factor authentication (MFA) are central to strong authentication, requiring users to provide two or more verification factors.
Types of Authentication Factors:
| Category | Examples |
|---|---|
| Something you know | Password, PIN, security question |
| Something you have | Security token, mobile app, SMS code |
| Something you are | Fingerprint, facial recognition, retina |
Benefits of 2FA/MFA:
- Reduced Risk: Even if a password is stolen, attackers cannot access accounts without the second factor.
- Compliance: Many regulations and standards mandate MFA for sensitive systems.
- Adaptability: MFA can be tailored to organizational needs, balancing security and user convenience.
Implementation Strategies
Assess Needs: Identify which systems and user roles require MFA, prioritizing high-risk accounts (e.g., administrators, finance). Choose Methods: Select authentication methods that fit your security requirements and user experience goals (e.g., app-based codes, hardware tokens, biometrics). Integrate with Existing Systems: Use identity and access management (IAM) solutions to streamline MFA deployment across applications. User Education: Train users on the importance of MFA and provide clear instructions for enrollment and use. Phased Rollout: Deploy MFA in stages, starting with the most critical accounts, to manage organizational impact and gather feedback. Continuous Review: Regularly audit and update authentication policies to address new threats and technologies.
Summary Table: Password Policies vs. MFA
| Aspect | Password Policies | MFA/2FA |
|---|---|---|
| Core Purpose | Ensure password strength and security | Add extra verification layers |
| Key Measures | Complexity, length, storage, lockout | Multiple factors (knowledge, possession, biometric) |
| Risk Reduction | Mitigates brute-force and guess attacks | Mitigates credential theft and phishing |
| User Impact | Can be burdensome if overly complex | Adds steps but greatly enhances security |
| Compliance | Often required by standards | Mandated for sensitive systems |
Conclusion
Implementing strong authentication requires both robust password policies and the adoption of multi-factor authentication. Together, these measures significantly reduce the risk of unauthorized access and data breaches, protecting both organizational and individual assets. A strategic, user-aware rollout ensures security improvements without undue disruption.