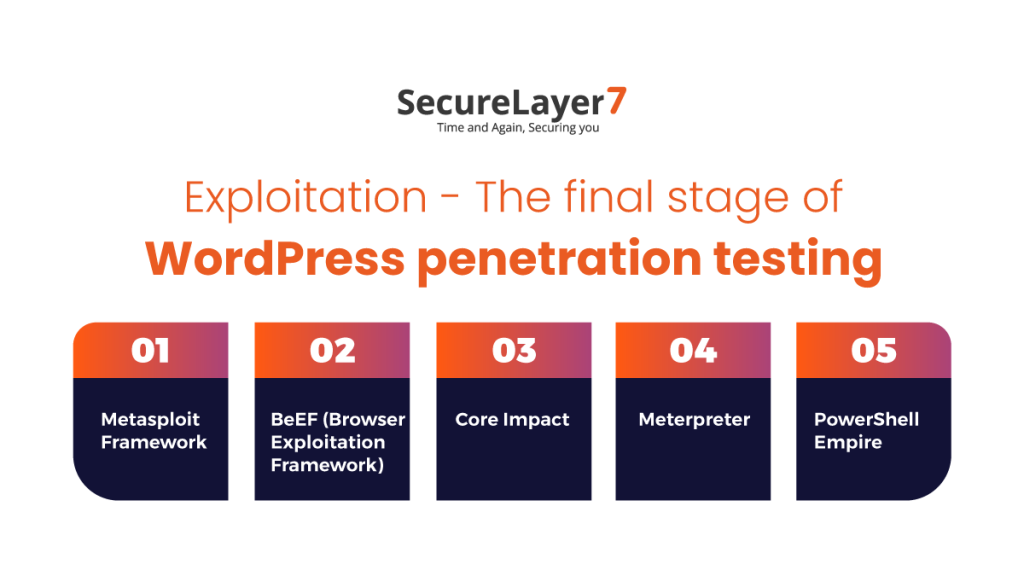
Conducting periodic security audits and penetration testing for WordPress involves systematically examining your site to identify vulnerabilities, followed by testing those weaknesses to prevent exploitation. This process should be done regularly—at least quarterly or more often for sensitive sites—to maintain robust security.
Key steps for periodic WordPress security audits include:
-
Run comprehensive security scans using trusted security plugins rather than online scanners, as plugins have deeper access to your files and database. These scans detect malware, vulnerabilities, and suspicious activity.
-
Keep WordPress core, themes, and plugins up to date to patch known vulnerabilities, as outdated software is a common attack vector.
-
Review user accounts and permissions, enforcing the principle of least privilege by removing inactive or unnecessary accounts and ensuring strong, unique passwords.
-
Install and properly configure a firewall, such as a web application firewall (WAF), to block malicious traffic before it reaches your site. Regularly review firewall logs for suspicious patterns and set up alerts for unusual activities.
-
Monitor site activity and analytics for anomalies like unusual login attempts, traffic spikes, or file changes that may indicate an attack.
-
Verify backups regularly to ensure you can restore your site quickly after an incident.
-
Check server security settings, including SSL certificates, file permissions, and database configurations, to prevent common exploits like SQL injection.
For penetration testing (pen testing), which simulates real-world attacks to exploit vulnerabilities:
-
Conduct pen tests after thorough security audits to validate the effectiveness of your defenses and uncover hidden weaknesses.
-
Use specialized tools and suites designed for WordPress security testing, such as WPAUDIT, which is tailored for ethical hackers and security professionals.
-
Penetration testing should cover all layers: WordPress core, themes, plugins, user roles, server environment, and network defenses.
-
Schedule regular vulnerability scans using tools like WPScan, which maintains a database of known WordPress vulnerabilities and can automate scans to detect new threats.
-
Combine automated scanning with manual review of logs, configurations, and code to ensure comprehensive coverage.
In summary, a cyclical approach of auditing, patching, testing, and monitoring is essential to maintain WordPress security. Regular audits identify vulnerabilities, penetration testing validates defenses, and ongoing monitoring helps detect and respond to new threats promptly.
This proactive, layered security strategy significantly reduces the risk of compromise and helps maintain the integrity and availability of your WordPress site.