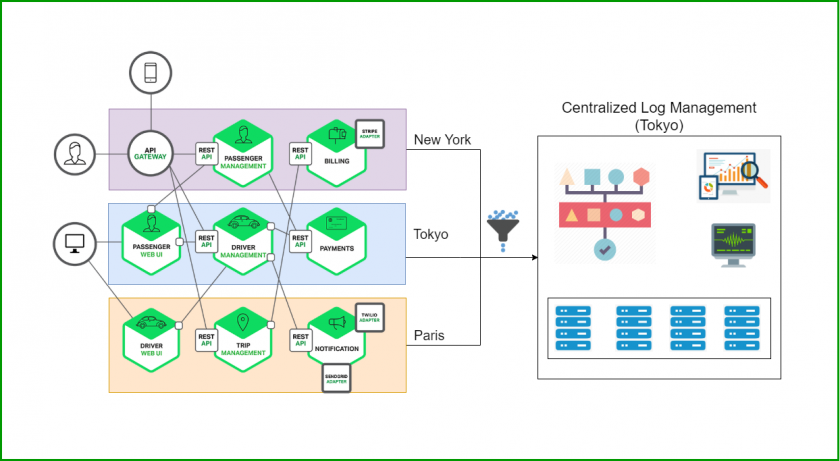
Monitoring logs and analytics enable early detection of security incidents by continuously collecting, analyzing, and correlating log data to identify anomalies, suspicious activities, and patterns indicative of cyber threats. This process allows security teams to respond quickly before attacks escalate, minimizing damage and improving incident response effectiveness.
Key points on how monitoring logs and analytics aid early detection include:
-
Real-time log monitoring and alerts: Immediate detection of unusual events such as unauthorized access, abnormal login times, or system behavior anomalies triggers automated alerts for rapid investigation and response.
-
Centralized log management: Aggregating logs from diverse sources into a single platform enhances visibility, reduces investigation time, and supports long-term trend analysis to detect stealthy or evolving threats.
-
Use of advanced tools: Security Information and Event Management (SIEM), Security Orchestration, Automation, and Response (SOAR), and AI-powered analytics platforms automate threat detection by correlating events, triaging alerts, and reducing false positives.
-
Threat hunting and behavioral analysis: Analytics enable proactive searching for hidden threats and identification of attack patterns, helping to uncover sophisticated intrusions that bypass traditional defenses.
-
Compliance and audit support: Monitoring logs also ensures adherence to security policies and regulatory requirements by flagging violations and maintaining audit trails.
-
Incident investigation and response: Detailed log analysis provides forensic data to understand attack vectors, timeline, and affected systems, facilitating containment and remediation.
-
Long-term analytics: Beyond immediate alerts, analyzing historical log data helps identify persistent threats, emerging attack trends, and system vulnerabilities.
In summary, effective log monitoring and analytics combine continuous data collection, automated analysis, and centralized management to detect security incidents early, enabling faster, more informed responses and strengthening overall cybersecurity posture. This approach is fundamental to modern security operations and risk management.