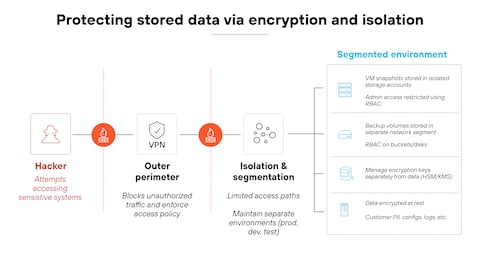
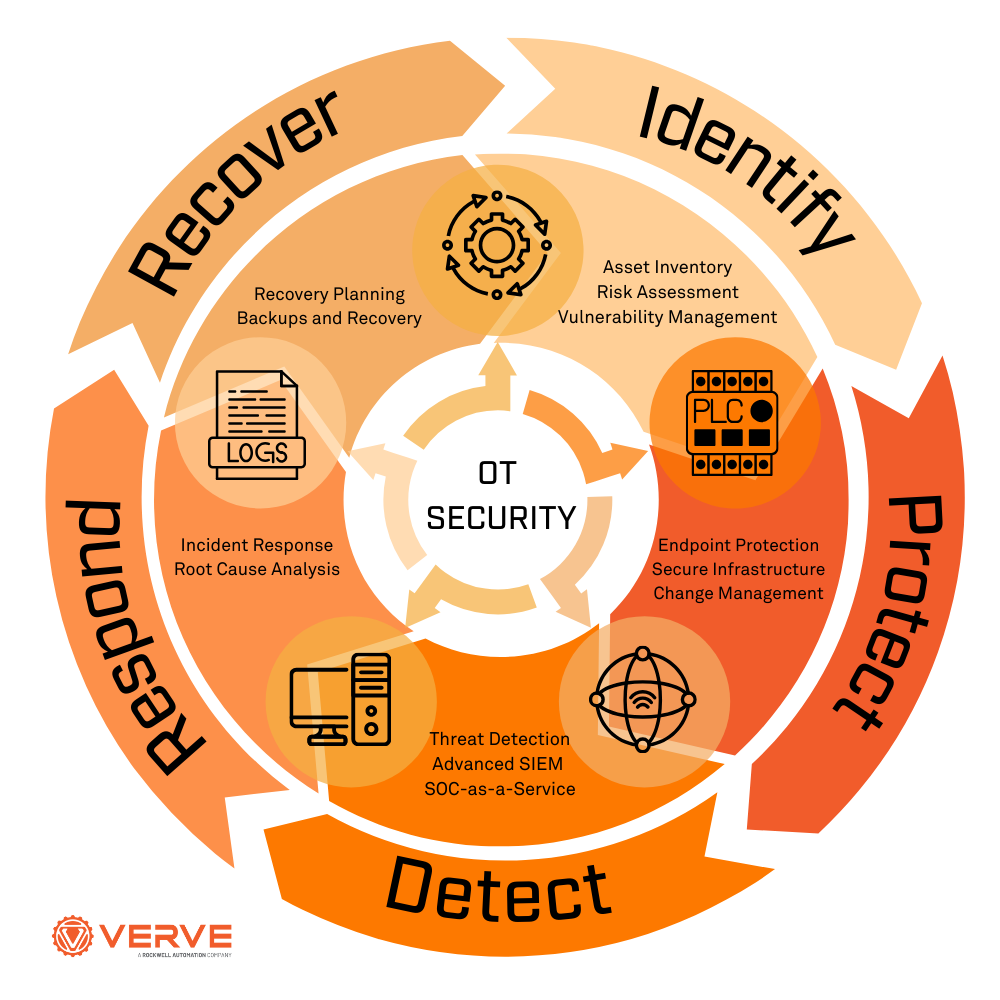
Advanced security tactics for protecting IT environments involve a combination of regular scans, continuous monitoring, and structured incident response to detect, contain, and remediate threats effectively.
Key components include:
-
Regular Scans: Conduct frequent vulnerability scans and malware scans on endpoints and networks to identify weaknesses and infections early. These scans help prioritize risks based on potential impact and ensure timely patching of software vulnerabilities to prevent exploitation.
-
Continuous Monitoring: Implement real-time monitoring using tools like Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM) systems, and behavioral analytics. These tools collect and analyze data from endpoints, networks, and logs to detect suspicious activities and anomalies indicative of cyber attacks.
-
Incident Response: Establish a formal incident response plan following standards such as ISO/IEC 27035. The process includes preparation (training and tools setup), identification (detecting and confirming incidents), assessment (evaluating impact), containment (isolating threats), eradication and recovery (removing threats and restoring systems), and lessons learned (post-incident review to improve defenses).
Additional advanced tactics include:
-
AI and Machine Learning: Use AI/ML to enhance threat detection accuracy and speed by analyzing large data sets and learning from new attack patterns, reducing false positives.
-
Zero Trust Model: Adopt a "never trust, always verify" approach where every access request is authenticated and monitored, limiting lateral movement of attackers within networks.
-
Automated Threat Remediation: Automate containment actions such as isolating infected endpoints, blocking malicious IPs, and disabling compromised accounts to reduce response time and limit damage.
-
Regular Testing and Assessment: Perform penetration tests, breach simulations, and vulnerability assessments continuously to identify and fix security gaps before attackers exploit them.
-
Strong Access Controls: Enforce multi-factor authentication (MFA), strong unique passwords, and privilege management to reduce the risk of unauthorized access.
Together, these tactics form a layered, proactive defense strategy that minimizes risk exposure, accelerates detection, and ensures rapid, effective response to security incidents.